Being in Berlin reminded me that I haven’t been around the hackers I know and love since my last round of gadget aquirement. A lot of conversations have been happening recently around the usability of crypto-aware tools (including an event in DC on Jan 11th that GWOB is doing with OpenITP – you should go!). What we fail to talk about are how easy many existing things are out there, and what they are. Here are some things we did:
Encrypt all the things!
Why this matters: when interacting with law enforcement, you can plead the 5th around your password, but the hardware itself can be seized, albeit sometimes for a short time. During this, they can take an image of your disk, IE, scan and copy anything on it. By encrypting your device, all they will see is adsfliu9p8aerkadfov8c79234hfgia etc instead of “ohai.”
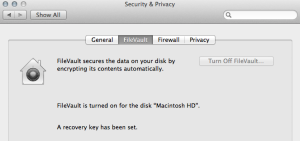
- A Mac. It’s not as hard as you think. With a solid state drive, it takes about 45 minutes. Let it run tonight while you head to bed. For a Mac, plug it in, launch System Preferences > Security and Privacy > File Vault > Encrypt.
- An Android. Also not difficult. Settings > Security > Encrypt Device. Again, you’ll need to leave it plugged in and have a bit of patience with it.
Password Management
Why this is important: helps you not fall into password reuse issues by allowing you to only remember one strong password, and loading in non-human-memorable passwords.
On Mac, I went for 1Password. It costs some money, but it’s hella easy to use, and I can share an encrypted file via dropbox between my multiple devices so I can still access accounts. While I’m plugging in these accounts to 1Password, I’m slowly changing all my less-secure passwords for randomized ones.
Communications
Why this is important: While we’ve achieved HTTPS in most places, within and between larger “clouds” data is not actually sent encrypted. In order for you to maintain your privacy, it’s important for anything you send to be encrypted. All of these are usable in the exact same way from a user standpoint as the things they replace. They just also encrypt the traffic. Try them out.
I already use Adium for Off The Record (OTR) and Thunderbird for Pretty Good Privacy (PGP) on my Mac. I’d use Jitsi but it crashes anytime I’ve tried. Waiting until it works. That said, I also want the messages I send on my phone to be encrypted.
- ChatSecure : chat on phone
- TextSecure : already installed, but worth mentioning
- Threema : also encrypts images etc! Let me know if you’re on it, definitely needs critical mass in order to be usable. I’m K69NNHXE
- Orweb : Tor browser on phone
- Orbot : Tor node on phone
Self-Hosting
Why this is important: you control your data. Or at least someone you can go punch in the face does. I am also incredibly hungry at this point of writing this post and thus this section lacks detail.
Uberspace : I like this group out of Berlin. They’re pretty great.
Ownweb : All the functionality of calendar, contact storage, etc. Works beautifully on Uberspace.
edit: Make that OwnCloud. Thanks, Natanji! Also, hosting on your own of course requires the mental and technical to maintain those servers.
Is it safe?
When is the last time you ran a backup? Why not right now?
<3 to all the fine folk who helped out with this : Tomate, Herr Flupke, Morgan.

I can’t find any info on “Ownweb” – did you mean “Owncloud”, perhaps? Or can you provide a link?
I personally would not use threema. While there are shiny, there is no way to check the implementation (at least) of their crypto. It is known that the NSA weakens crypto and their implementation [1]. Threema wouldn’t be the first Swiss crypto-product with a backdoor[2]. You run their unchecked code on your intimate device after all.
[1] https://www.schneier.com/blog/archives/2013/10/defending_again_1.html
[2] https://en.wikipedia.org/wiki/Crypto_AG#Back-doored_machines
@gdbelvin glad to see a more complete version of a similar thing I wrote a year and a half ago… http://t.co/GDhOU8EkGa